Reporting Simulated Phishing Attacks (Cyber Defenders)
Cyber Guru Phishing can record reports made by users who, correctly, are able to recognize phishing attacks and report them to the appropriate department.
This article describes the procedure necessary for these reports, to be recognized and recorded by the Cyber Guru system to enhance the "Reported Attacks" data.
This function will allow the Cyber Guru Phishing platform to analyze the data of Reported Emails, so that a profile can be enhanced, which in the pathway is called Cyber Defenders. Cyber Defenders are the Users who, not only recognize and do not click on the program's simulations, but also report the suspicious e-mail internally.
⚠️ | ATTENTION: The system does not record reports received from a user who has FIRST clicked on the simulation and ONLY AFTER the click proceeded to report it. |
The way the user reports a hypothetical phishing simulation e-mail may vary depending on the organizational needs of the client and the operational possibilities offered by the e-mail management infrastructure.
The most widely used and simple tool for the user is the configuration of a "Report Phishing" button to be made visible in the organization's mail client, whether application-based (e.g., Microsoft Outlook), Web-based (such as OWA or Google Gmail), or mobile device-based (e.g., Outlook for Android or iOS).Where it is not possible or desired to use the button there are other options for performing reporting, as discussed in the following sections.
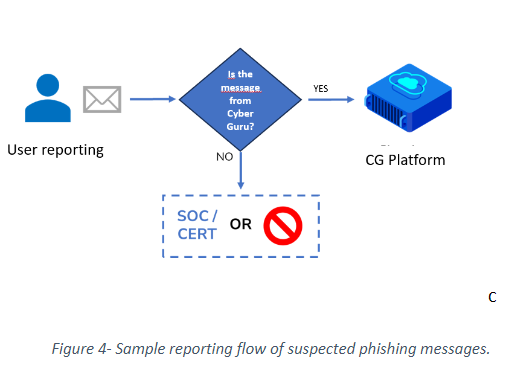
Regardless of the use of the reporting button, the mail flow to the CG Platform may integrate with any existing mail flow to the client. It is important that the reporting flow performs a filter with the goal of sending to the CG Platform only phishing simulation messages that it has sent to the user, excluding any other irrelevant messages. Messages that are not from Cyber Guru can be blocked or can be routed to the client's SOC/CERT for analysis from a cybersecurity perspective
Keep in mind that regardless of the effectiveness of the filter placed in the forwarding flow, the CG Platform automatically discards forwarded messages that do not belong to the submitted phishing simulations.
Conditions for submitting a report to Cyber Guru
The necessary and sufficient conditions for a report to be registered within the CG Platform are listed below:
An e-mail must be sent for each report from each user, to defenders@cyberguru.report;
The email can be forwarded directly (in-body message) or sent as an attachment;
Regardless of the mode chosen (in-body or attached), the report must contain at least the particle "?rid=" followed by the RID identifier (this is an alphanumeric code that varies for each campaign, user, client).
The above methods can be performed through automated systems, such as using an appropriately configured report button, or through manual actions (e.g., the user forwards the message to be reported to defenders@cyberguru.report or another address in the organization, which in turn filters the report and forwards it to Cyber Guru). The following are listed as examples of some scenarios in which the system correctly records reports received:
User independently forwards phishing email to defenders@cyberguru.report
The user forwards that email to a colleague/IT manager/other who in turn forwards it back to defenders@cyberguru.report
User forwards such email to a ticketing system from which the email is subsequently forwarded to defenders@cyberguru.report
The user forwards such an email, from which the phishing link (ending in "?rid=IDENTIFICATION") is extracted, this link is inserted into an email which is in turn forwarded to defenders@cyberguru.report
The following are listed as examples where the system does not record correctly
reports received:
A list of email addresses is sent
A list of usernames is sent
A list of rid is sent
An email address is sent
A username is sent
A RID code without particle "?rid=" is sent.
Procedure for automatic routing of reported mails.
In order to create a filter capable of correctly routing reports of emails that the user suspects of being simulated or real phishing, some static elements have been inserted into the emails sent by the platform to allow automatic recognition:
• All the URLs contained in the e-mail have the particle “?rid=" inside;
• Unless otherwise agreed, the static IP of origin of the simulated phishing emails is 85.235.135.191;
• All emails have a personalized header with name "CGRE" and value "en2358nfwf348fnw932jdo4fe4rrewffd";
• All emails have an HTML tag included in the message body "<div class=”CGRE- en2358nfwf348fnw932jdo4fe4rrewffd”>";
• Emails forwarded through Microsoft's “Report Phishing” button have the string “client-ip=85.235.135.191” in their body; helo=phishing.cyberguru.report”.