False positive management
If unusual results are observed during a phishing campaign, it is possible that they are false clicks. The presence of false clicks can come in the form of unusually high click-through rates, even 100 percent, or with the presence of IP addresses that do not belong to the client's infrastructure. Below are some of the most common reasons for false positives and some suggestions for dealing with them.
⚠️ | ATTENTION: Cyber Guru pays great attention to all aspects that contribute to the quality of the data in detecting user actions. However, as is the case with any phishing simulation platform, it is not possible to exclude beforehand that one or more automated systems present in the customer's email management infrastructure may generate clicks in the absence of user interaction. For this reason, the customer is encouraged to carefully read the instructions in this chapter and periodically check the report documenting the generation of clicks in order to exclude the intervention of unwanted automatism. Cyber Guru is available with technical support to guide the customer, who remains responsible for the detection of false clicks and the configuration of their systems. |
What is meant by click?
Clicks" are how we track when a user clicks on a phishing link in a simulated e-mail. However, there are other ways in which a click can be recorded. Clicks that were not caused by a user action on a phishing link are called "false positives." Some common reasons for false positives are listed below::
Incorrect whitelisting that may cause automatic clicks or "bot clicks."
Spam filter may require additional whitelisting to exempt simulated phishing emails from link analysis or link probing;
Mail filters with additional security packages that were not whitelisted;
Security or antivirus software for endpoints;
Link preview functions in mobile device operating systems;
Security software embedded in mobile device management (MDM) systems;
Phishing emails forwarded by one user to another user. This click may be recorded because the forwarded e- mail was sandboxed and checked by the mail server or because the recipient of the forwarded e- mail clicked on the link.
How to identify "bot clicks"
Errors or deficiencies in whitelisting can lead to the so-called "bot clicks." These clicks are generated by automated processes present in the security devices within the customer's infrastructure, both locally and in the cloud.
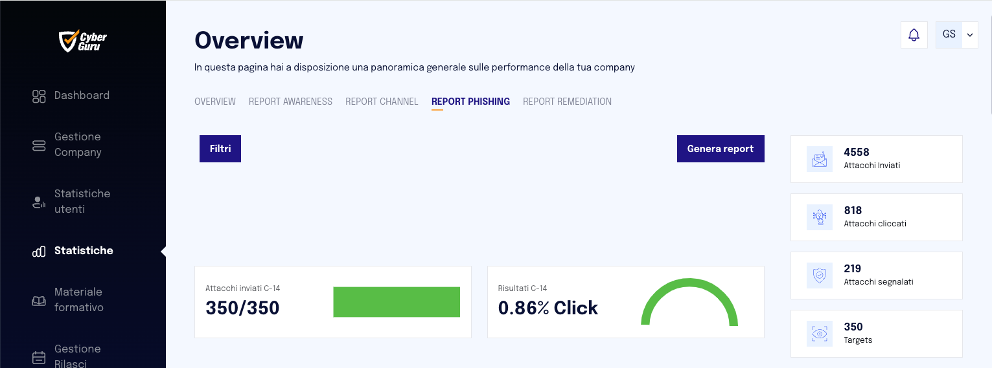
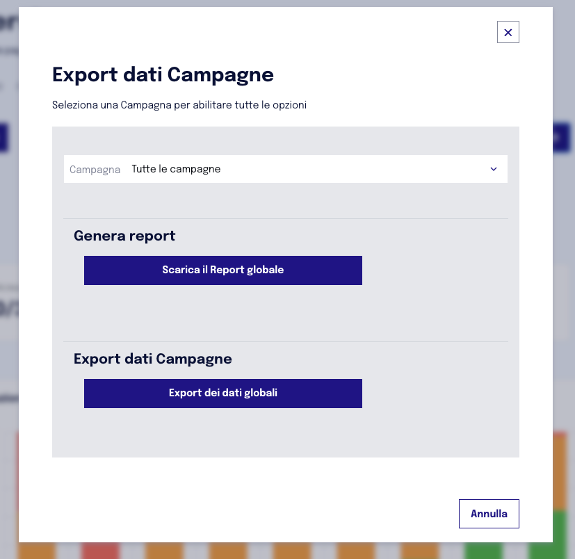
To identify bot clicks, it's possible to examine the results of phishing campaigns through the CSV report generated by the "Generate Report" function available in the "Statistics" module. It's necessary to select "Export dei dati globali," as shown in the reference images. This report could provide information to distinguish clicks generated by automated behaviors from those made by real users
Listed below are some ways that bots might identify clicks:
The "phished browser" column indicates that the browser or its version is not used in your environment or is obsolete;
The operating system listed is one that users do not have access to in your environment;
The IP address belongs to a provider of one of your security products.
What causes unexpected IP addresses in campaign results??
When a click is recorded by Cyber Guru, the IP address where the "click" came from is recorded. Below are some examples of the reasons why unexpected IP addresses may be displayed:
If a user is on a mobile device and clicks on the link, the click may be displayed as coming from the cellular service provider;
If a user is connected to the home Wi-Fi network, the click is recorded as coming from an Internet service provider (ISP) IP address;
If a user is on a public Wi-Fi network, the click will be recorded from the location where the user was at the time of the click;
If you or one of your products uses a hosted service provider, such as AWS, the IP address may come from another location or even another country.Some link analysis processes may not occur on the client side and the link may be "passed" to the security provider's backend processing or analysis center;
If the URL is sent to VirusTotal, the IP address may come from another location. This link may be sent automatically by a used product or by the user. When a URL is sent to VirusTotal, it analyzes the URL to determine if it should be added to the threat definitions as hostile. Sometimes the link analysis is immediate. Other times it may occur over the course of several hours. These IP addresses can be registered as security providers or ISPs. .
What can I do to avoid false positives?
Knowing your infrastructure is the most important step in preventing false positives. Since there is a wide variety of security software products, you should check the documentation of the software or service providers you use to see if there is a section that exempts links or domains from link scanning, link analysis, or link probing.
You can also run test campaigns with a couple of different simulation emails on machines that have the same configuration as the users' workstations. These test campaigns can help to understand whether the current configuration may be causing false positives.
If Microsoft's "Report Phishing" button is used, make sure this is configured correctly so that no additional analysis is done to the emails received by Cyber Guru.
Check whether the security products have the additional whitelisting option. If you can, include the phish link domains and landing page domains used by the CG Platform in the whitelisting configuration. This extra step can help prevent false positives.