SCIM Configuration with Microsoft EntraID
Client-Side Configuration Example
Below is the client-side configuration with Microsoft EntraID.
Prerequisites:
Customer has received the tenant URL and token from Cyberguru.
Customer have implemented the SSO configuration with Cyberguru.
Procedure
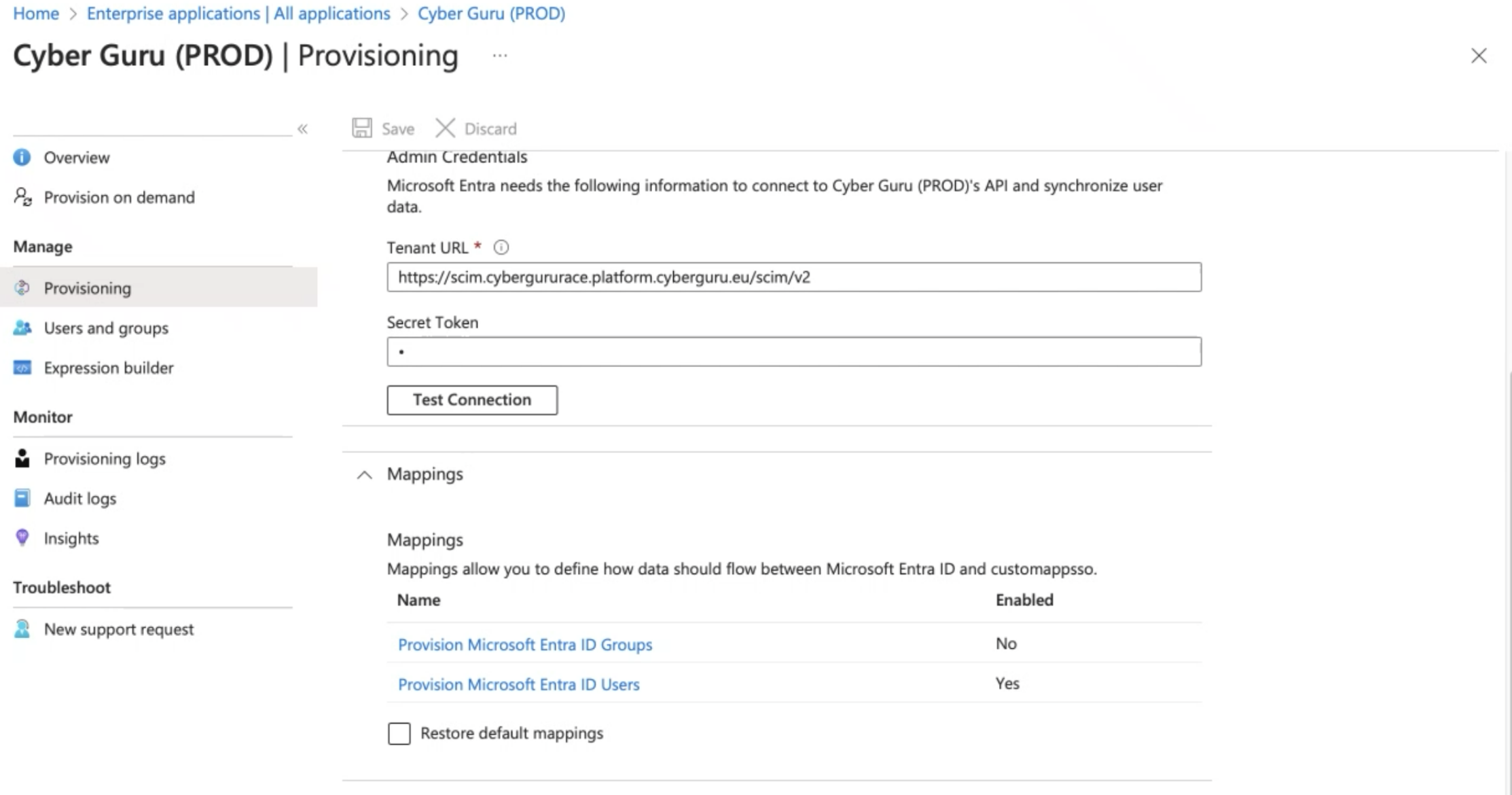
In the Application created for SSO
Proceed to Manage -> Provisioning and configure:
Provisioning mode: "Automatic"
In the Admin Credential Section
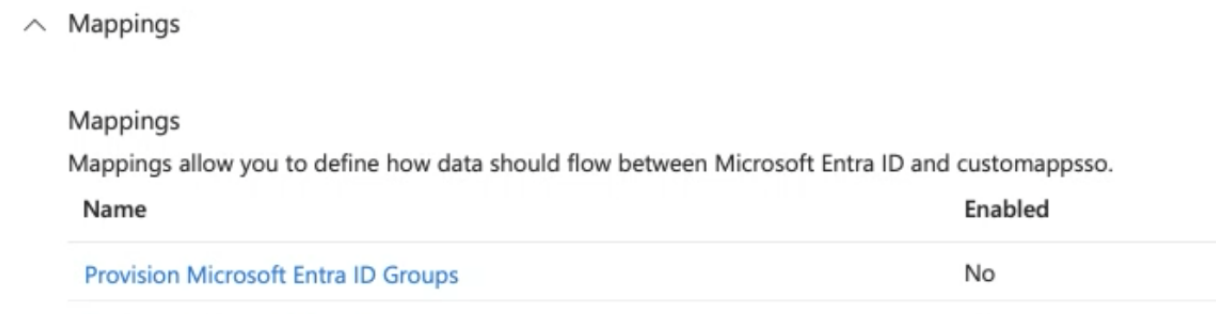
In the Mapping section:
Disable group provisioning (in "Provision Microsoft Entra ID Groups" and set "Enabled" to "NO")
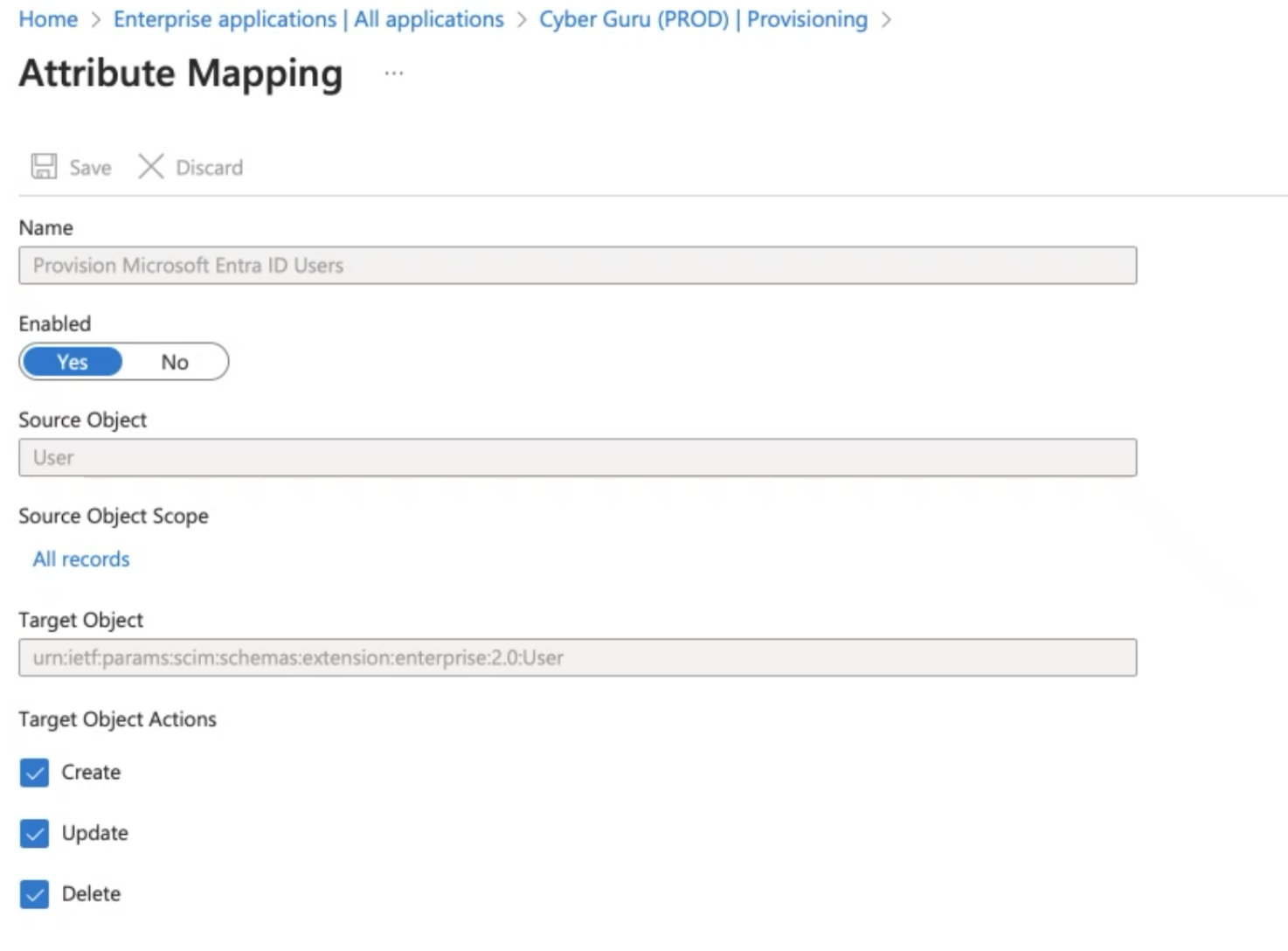
In "Provisioning Microsoft Entraid Users" configure the User mapping:
Target object actions: check "Create", "Update", "Delete"
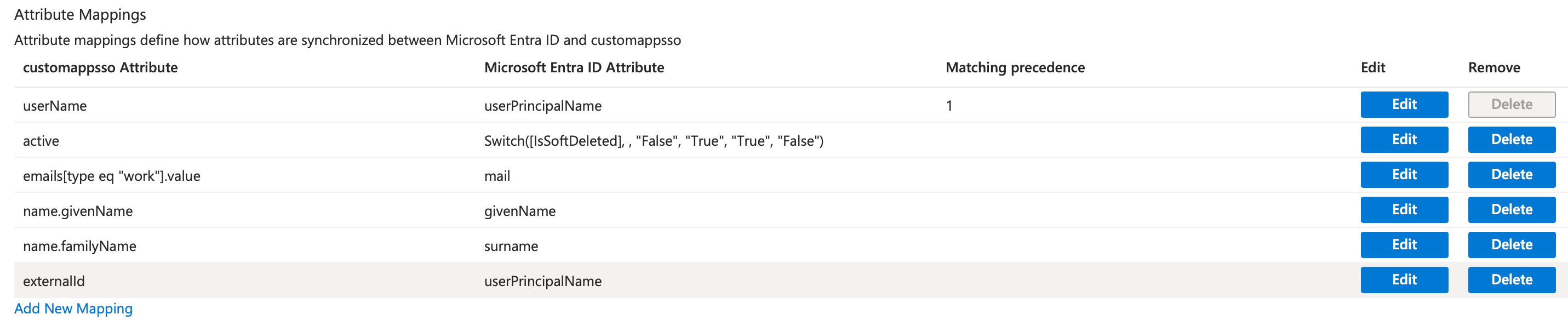
In Attribute Mappings configure:
required:
userName -> mail
active -> Switch([IsSoftDeleted], , "False", "True", "True", "False")
emails[type eq "work"].value -> userPrincipalName
externalId -> mail
supported not required:
name.givenName
name.familyName
addresses[type eq "work"].country
phoneNumbers[type eq "work"].value
locale
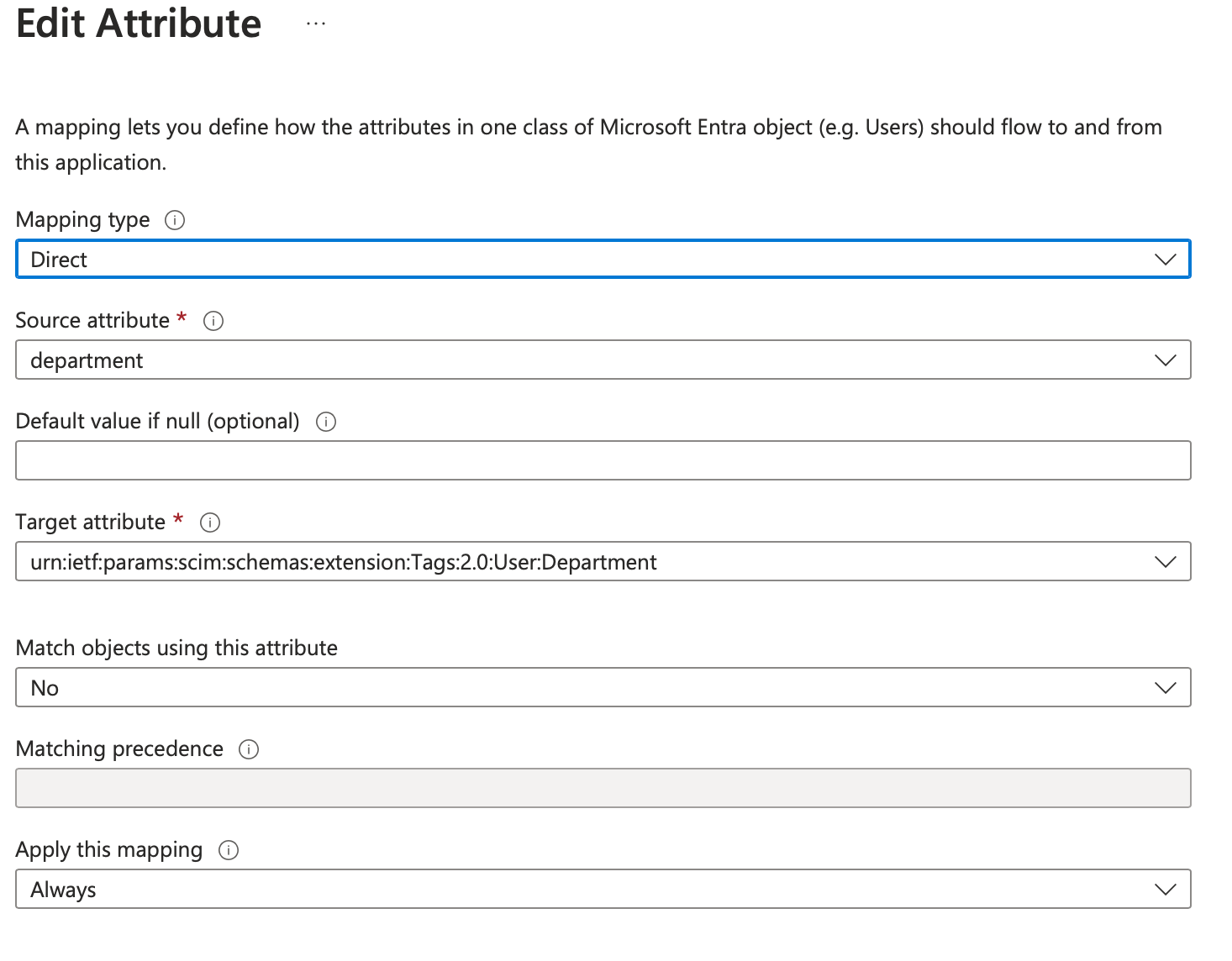
to provision the org add a custom attribute mapping:
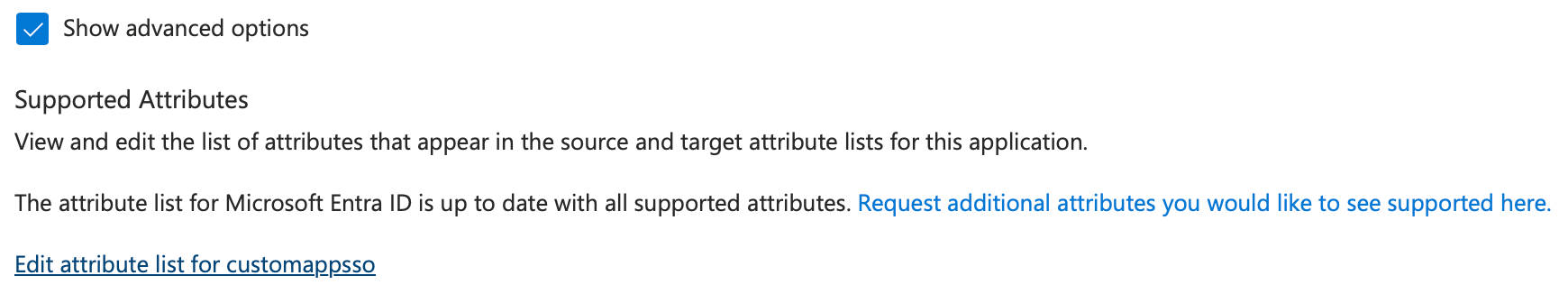
check on "Show advanced options"
click "Edit attribute list for customappsso"
scroll to the bottom of the mapper list and add in the last row a mapper of the form: urn:ietf:params:scim:schemas:extension:Tags:2.0:User:[org-name]
Save and return to the "Attribute Mapping" section
click "Add New Mapping"
"Mapping type" -> Direct
"Source Attribute" -> the attribute to map in the org
"Target attribute" -> urn:ietf:params:scim:schemas:extension:Tags:2.0:User:[org-name]
click on OK