QR CODE ATTACKS
How it works and types of attacks
QR Code attacks can be managed in two ways:
paper format
email template containing a QR code
This way, greater flexibility is offered on how to distribute the attack.
The ability to carry out a QR code attack is guaranteed to companies that have purchased the "Phish Pro" add-on and activated the related licenses.
NB. The indicated add-on can be activated exclusively following the purchase of the "Phish Pro" component for the specific Organization. No activation is allowed for testing or trial purposes. If necessary, it will be essential to contact our support in advance.
Paper QR Code
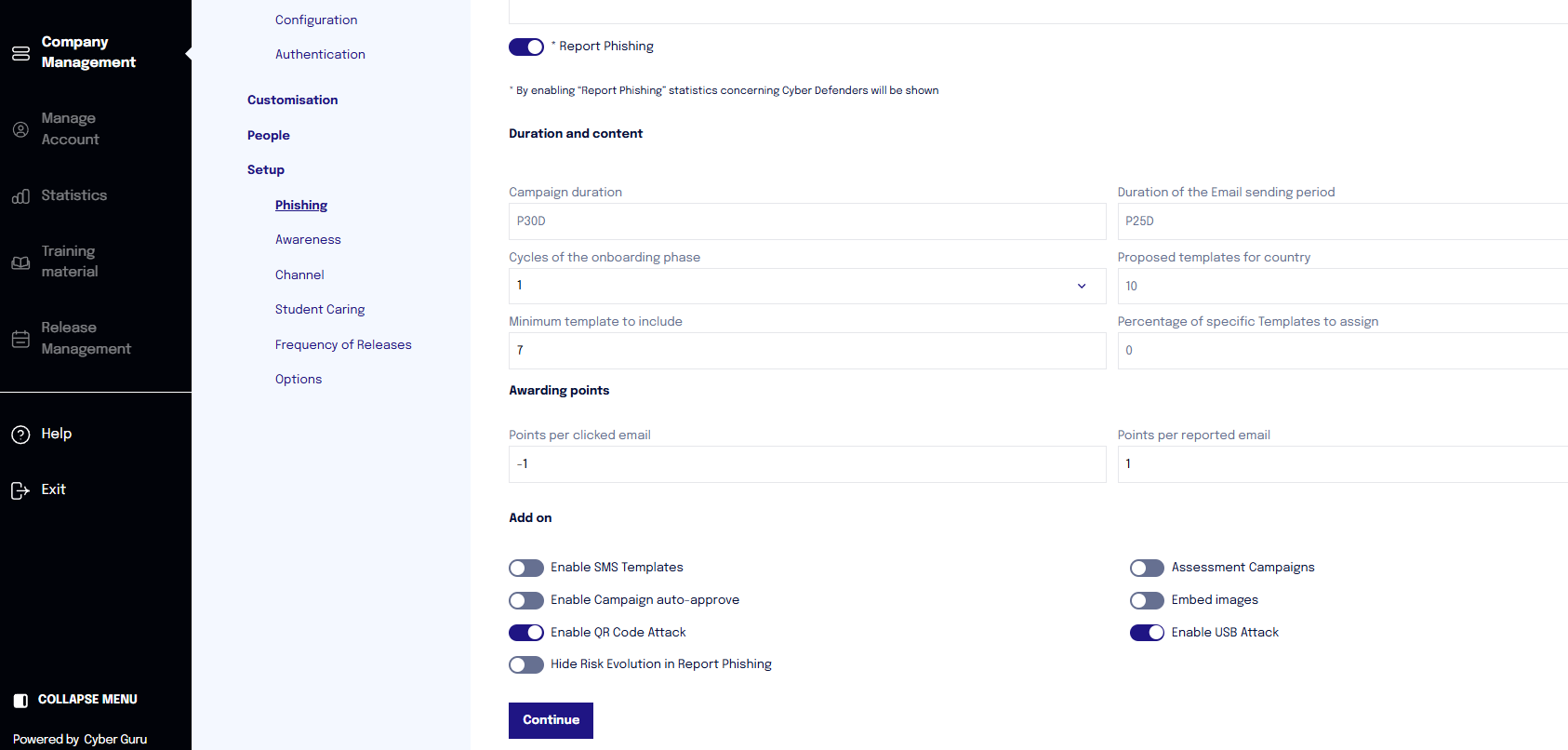
To enable the QR code attack, it is necessary to activate the toggle "Activate QR Code Attacks" available in the section "Company Management > Setup > Phishing".
Once the toggle is enabled, you must proceed with the customization of the QR code by associating the landing page you want to use.
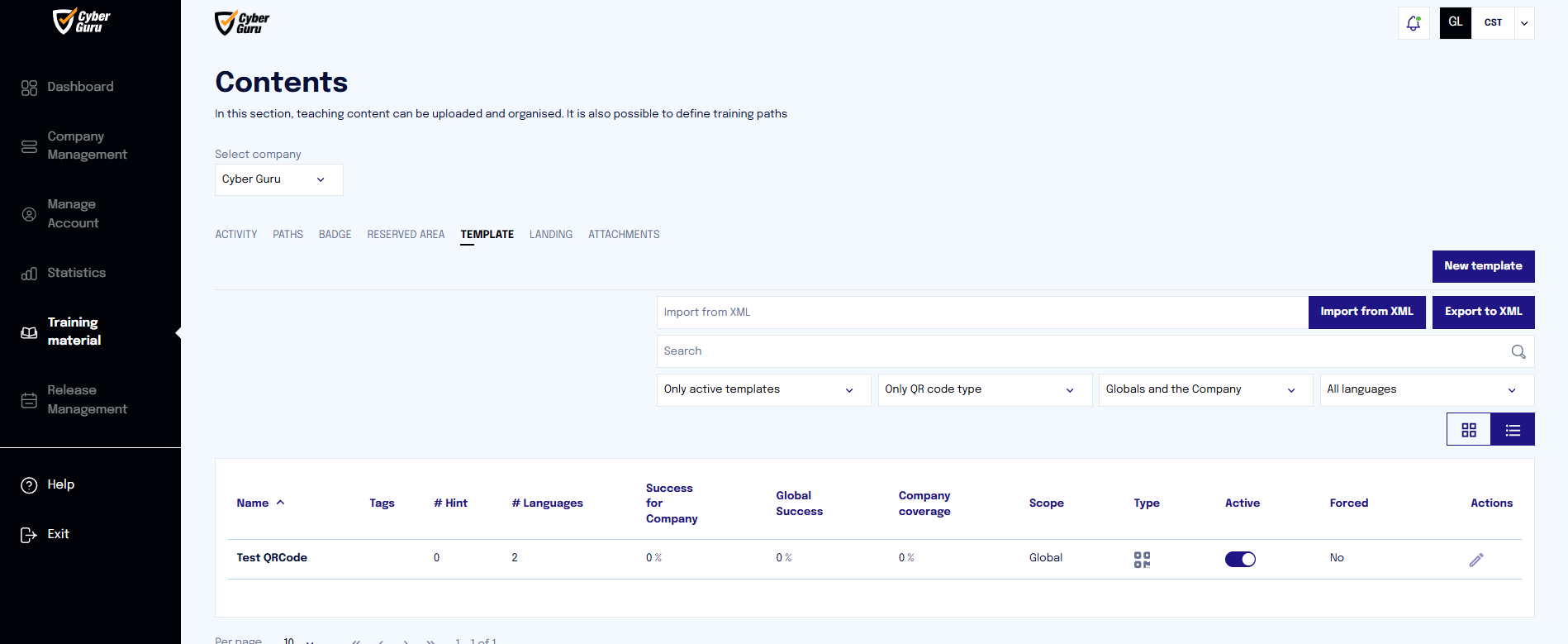
To do this, you can select "Informational Material", choose the company of interest, and finally "Template". You proceed by indicating in the menu that allows filtering templates by type "Only QR code type templates".
The global template displayed must then be copied to the company where it will be used.
To copy the template, simply click on the pencil icon in the actions column and select the "Actions" section. A dropdown menu at the bottom shows the subdomains of the companies where the template can be copied.
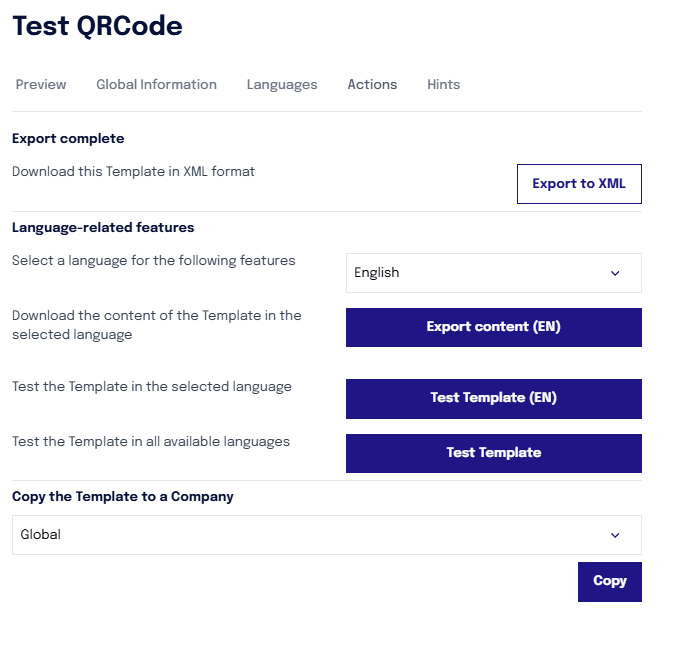
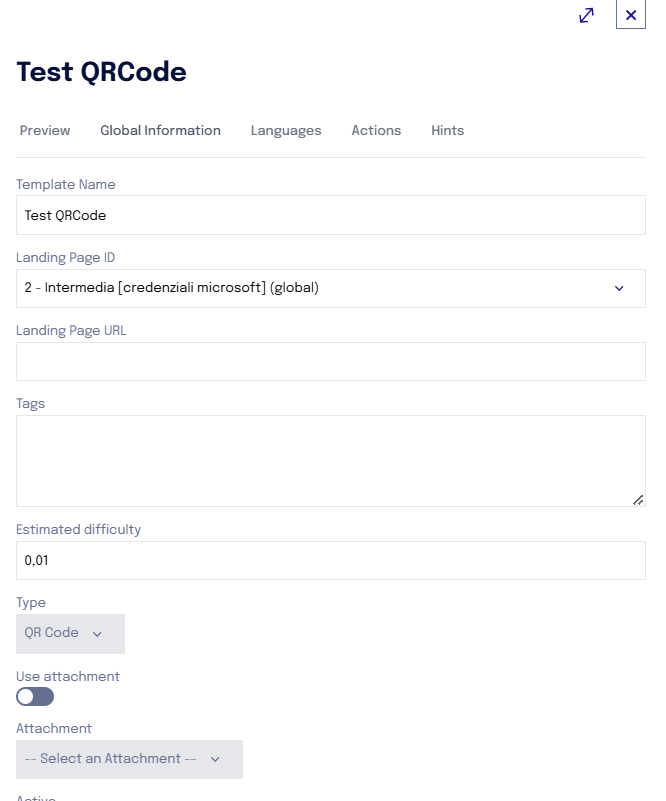
Once the template has been copied, becoming a "company template", it can be customized
by modifying the text of the email that will be sent to the contact containing the QR code to be printed
by choosing which landing page to associate
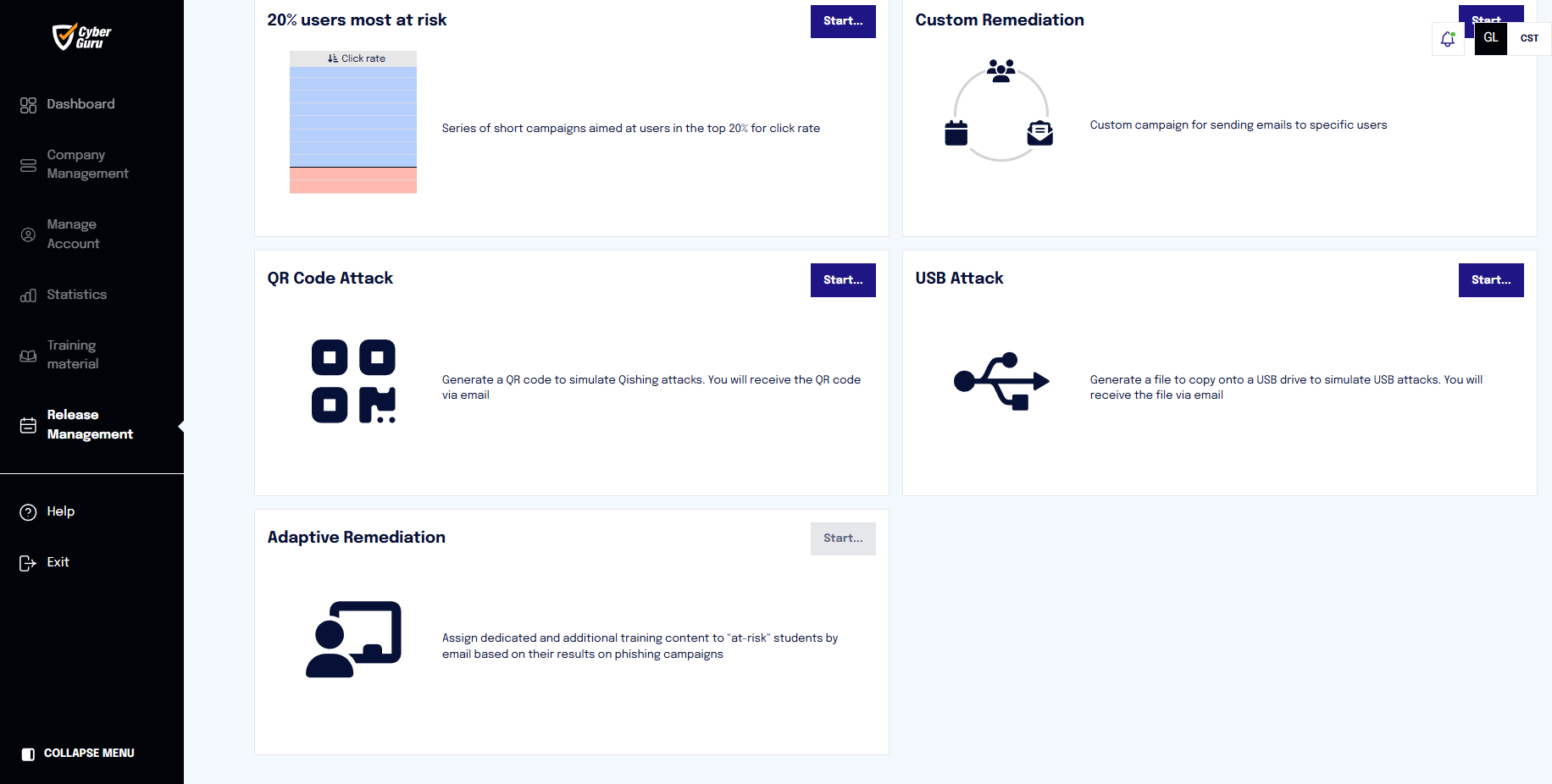
At this point, you can click on the section "Release Management > Remediation > QR Code Attack"
NOTE: Although it is within the remediation panel, the QR Code campaign can also be activated in the absence of campaigns conducted in Cyber Guru Phishing.
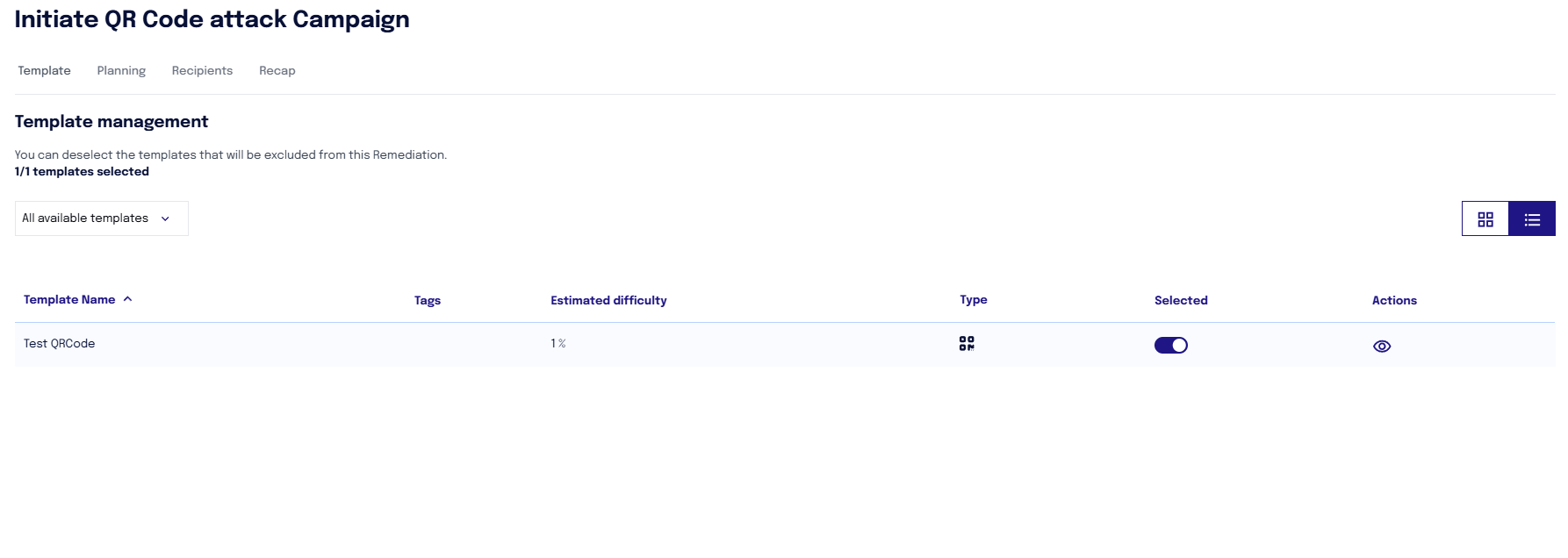
By clicking "Start", a screen opens where you can view the template containing the QR code. This template is functional only for sending to the contact the QR code that must then be printed.
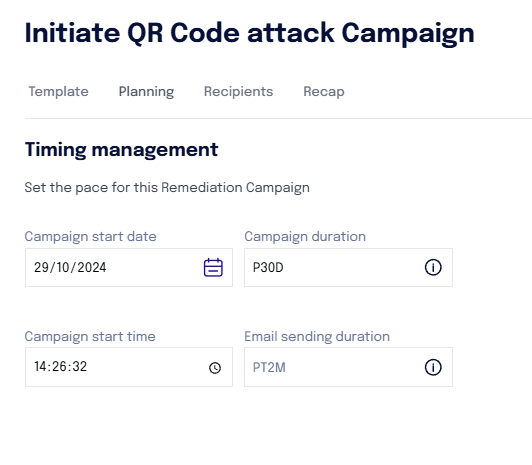
In the "Dates" section, you can indicate the duration of the campaign underlying the attack.
You must indicate:
the start date of the attack's validity (from when user interactions with the QR code will be recorded)
the duration of the campaign (for how long the system will record user interactions with the QR code). ANY EVENT AFTER THE ESTABLISHED DURATION WILL NOT BE RECORDED ON THE PLATFORM.
The start time of the campaign
In the "Email Sending Duration" field, it is necessary to leave the default value PT2M, which indicates that the email to the contact will be sent within 2 minutes.
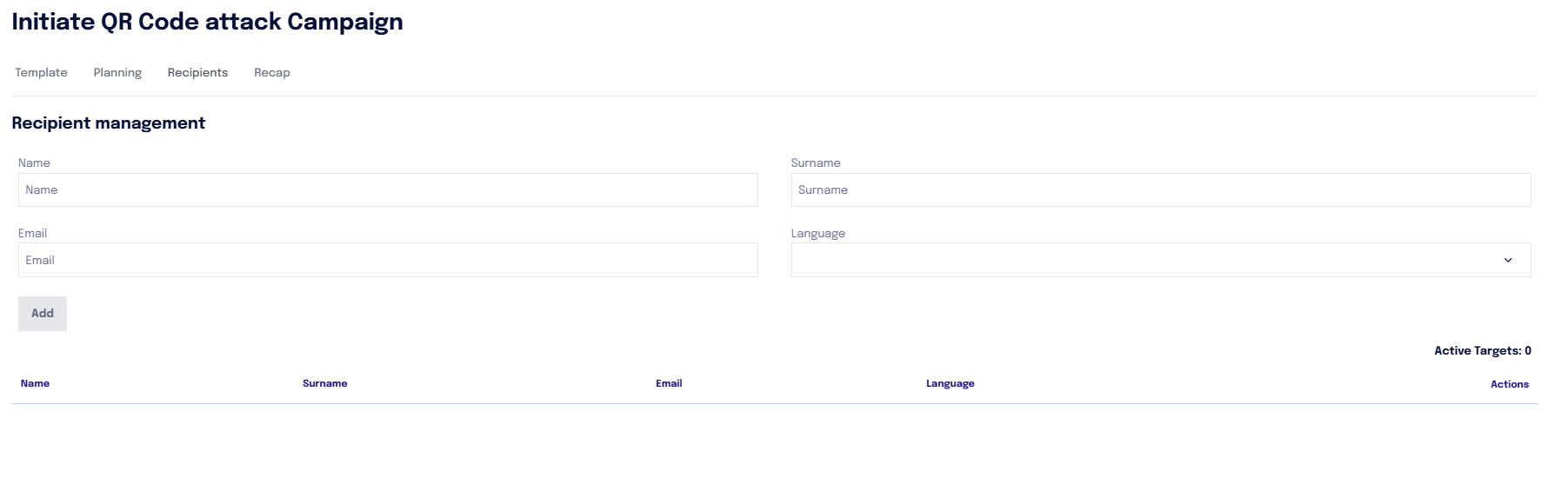
In the "Target" section, you can enter the first name, last name, email, and language of the user (contact) who will receive the QR code via email.
The QR code can also be sent simultaneously to multiple contacts.
In this section, the targets of the campaign should NOT be indicated, as a QR code attack is being defined without predetermined targets (anyone could scan the QR code).
Once the information has been entered, the supervisor receives a QR Code that can be printed and physically distributed.
Tracking interaction with QR code
When a user scans the QR Code, they are redirected to a phishing link.
There are two levels of tracking available:
Level 1: Anonymous tracking of the number of people who followed the link after scanning the QR Code.
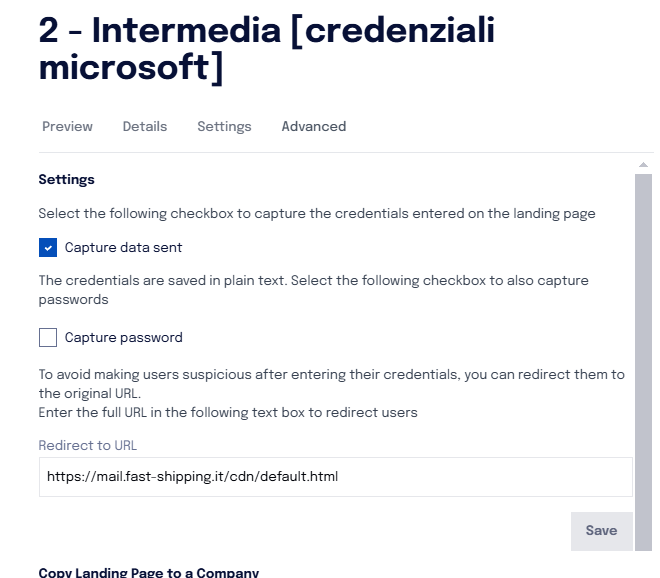
Level 2: If the user enters information (e.g., username and password), tracking becomes more detailed and can be configured to capture specific data fields. This second scenario can occur by inserting an intermediate landing page after scanning the QR Code.
Note: The entered passwords are not saved unless the password capture option is explicitly enabled within the landing page.
Once the remediation is complete, the data will be viewable in the "Statistics > Remediation Report" section.
Within the reporting, the following can be viewed:
The IP from which the click originated
Any information entered in the intermediate landing page
QR Code via email
A more advanced option that allows for greater traceability is sending QR Codes via email.
In this case, tracking is no longer anonymous but detailed like any normal phishing email campaign.
It is recommended to use the QR Code via email as it offers complete tracking and greater accuracy in results.
If you want to carry out a campaign with a template containing a QR code, it will be necessary to copy the template to the company of interest (keeping the global template inactive) and customize it as indicated above.